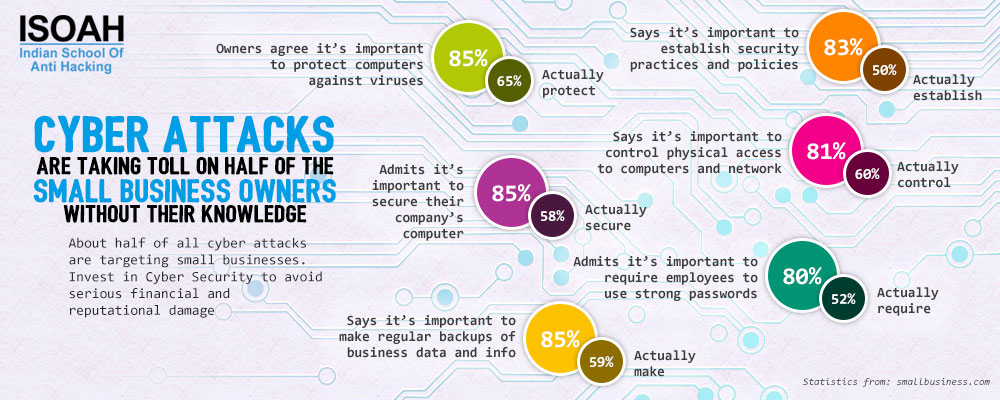
46% of organizations fail to learn even after massive cyber attacks
Article: Cyber Security

With the advancement of technology, organizations are facing sophisticated cyber attacks which are more dynamic, diverse and increasingly damaging. Data security has become a primary concern for organizations because an attack can cause huge financial repercussions and reputational damage. According to the CyberArk Global Advanced Threat Landscape Report 2018, 46% of IT security professionals rarely change their security strategy even after they are hit by a cyber attack. It is termed as 'cybersecurity inertia' which is putting sensitive data, infrastructure, and assets at risk.
There is a range of costs involved in a data breach. If there is any financial transaction happens as a result of the breach, the company has to bear the loss. The company has to compensate the affected customers, pay for the right measures to ensure security so the breach doesn't happen again. The cost is going to drastically increase with the implementation of General Data Protection Regulation (GDPR) which will be effective from May 2018.
What are the key findings of the report?
- 36% reported that their administrative credentials are stored in Word or Excel documents on company PCs.
- 46% said their organization can't prevent attackers from breaking into internal networks each time it is attempted.
- 50% admitted that their customers' privacy or personally identifiable information (PII) could be at risk because their data is not secured beyond the legally-required basics.
- 89% of IT security professionals stated that IT infrastructure and critical data are not fully protected unless privileged accounts, credentials, and secrets are secured. Yet 49% of organizations have no privileged account security strategy for the cloud.
Every organization has some valued sensitive data which are targeted by hackers and greater investment in cloud technologies and DevOps processes means expanded attack surface. Attackers continue to target and exploit privileged accounts, credentials, and secrets to accomplish their goals.
Secure Privileged Accounts:
The proportion of users who have local administrative privileges on their endpoint devices have drastically increased. It was 62% in 2016 survey whereas it has reached to a significant 87% in 2018- this jump perhaps indicates that employee demands flexibility have been allowed to trump security best practices.
Currently, the greatest cyber threats that the companies are facing include Phishing attack, ransomware, malware, attack on unsecured privileged accounts, unsecured data storage in the cloud etc.
As observed by the report, the automated processes inherent in cloud and DevOps mean that privileged accounts, credentials, and secrets are being created abundantly. If compromised, attackers would achieve lateral access to sensitive data across networks, data, and applications or can use cloud infrastructure for some more heinous activity like illicit crypto mining.
Cyber Inertia Leading To Data Breach:
Though the companies are well aware of the security risks, they have a relaxed approach towards cloud security. It is very evident from the fact that almost half of the organizations responded that they have no privileged account security strategy for the cloud. 68% are still relying on built-in security capabilities.
Cloud adoption has dramatically increased in recent years. As per the report, there is still limited understanding of the challenges of securing cloud workloads in IaaS (infrastructure as a service) and PaaS (platform as a service) environments. There is lack of understanding about who is responsible for security in the cloud. Though, the public cloud suppliers are clear that the enterprise is responsible for securing cloud workloads. Survey reveals that 86% of IT professionals feel security should be a regular board level discussion topic where 44% said they reward employees who prevent an IT Security Breach. Security is often considered as the concern of IT department only. But everyone in an organization should address some basic guidelines to ensure security. To achieve that, top management should take initiative to bridge the communication gap among employees. Investing in regular red team exercises could help organizations to identify where to focus and prioritize risk reduction.
Changing the Security Culture:
"Attackers continue to evolve their tactics, but organizations are faced with cybersecurity inertia that is tipping the scales in favor of the attacker," said Adam Bosnian, executive vice president, global business development, CyberArk. Companies must address a data breach with greater urgency. The priority should be to recognize the scope of an attack and examine how to minimize the impact and return to normal operations. Companies should proportionately spend on security. Currently, it is not invested proportionately to the value of the asset that is being protected, or on securing privileged access to that asset, the report said.
While targeting organizations, attackers are often successful at penetrating traditional perimeter defenses that haven't moved with time. Companies must show greater urgency to treat the risks associated with cybersecurity to protect the company from financial harm and reputational damage. For this, it is necessary to understand the security attack surface related to privileged accounts, and how it puts organizations at risk. To overcome the inertia, it requires strong leadership, accountability and defined security strategies. It is also important to communicate the strategies clearly and adopt a ‘think-like-an-attacker' mindset.