
Article: cyber security, cloud security
Discover how hackers use trusted app updates to sneak into your data — and how you can stay protected.
Details
Article: data protection and security, GDPR
GDPR compliance isn't just about dodging fines—it's about securing your business, protecting your reputation, and earning customer trust in an era where data breaches can be catastrophic.
Details![AWS Security Assessment: The Hidden Risks [2025] You Can't Ignore AWS Security Assessment: The Hidden Risks [2025] You Can't Ignore](images/aws-security-assessment-the-hidden-risks-2025-you-can-t-ignore.jpg)
Article: AWS Security
Imagine waking up to find your critical data stolen, your systems compromised, and your business paralyzed - all because of a security gap you didn't fix in time.
Details
Article: Cyber Security
Cyber threats targeting Azure environments are increasing at an alarming rate. If you're not continuously assessing your cloud security, you are at risk of major data breaches, compliance failures, and financial losses.
Details
Article: Internet Security
Partnering with ISOAH can improve your Docker security posture, protect your apps, and maintain your client's trust. Ensure your containerized apps remain secure against masked threats.
Details
Article: Internet Security
Our engagement in online activities often exposes our personal or sensitive information to unwanted people's attention. Each time we surf on the net, our data is garnered by different parties (websites, search engines, browsers etc.).
Details
Article: Cyber Security
As a reputable member of cyber security, we help our readers with every possible way to prevent them from the black hat hackers. We timely post helpful resources and share important tips to avoid any cyber-attacks from the phishers.
Details
Article: Coronavirus, Cyber Security
Fighting the Corona virus with the help of technology has its own perils which we must take care of.
Details
Article: cyber security
Be prepared with your list of to-dos in case you and your smartphone get fatally separated.
Details
Article: data protection and security
Despite the Data Protection Bill, a number of companies in India have fallen prey to information mishandling leading to chaos with hardly any of the organizations admitting their internal data fiasco.
Details
Article: cyber crime india
Indiscriminate usage of digital devices is spelling doom on the financial fortune of the sub-continent.
Details
Article: cyber security
Facebook re-emphasizes parental control over Messenger Kids, its juvenile messaging app.
Details
Article: ebike hacking
Electric scooters are more than just a smart ride as they are increasingly posing privacy issues to the riders.
Details
Article: IoT
A new set of IoT laws are in the making to rule the new world of the Internet of Things.
Details
Article: Cyber Security
A man who is a cyber security professional loses his secret banking credentials to fraudsters feigning to be Fastag experts on behalf of reputed banking institution leading to loss of Rs 50,000 and more.
Details
Article: Data Protection
The retired Supreme Court judge B.N. Sri Krishna says that the Personal Data Protection Bill is not in tandem with the draft that was designed for the same.
Details
Article: Ransomware
A latest avatar of Vega Ransomware out in the wild across continents targeting health and technology.
Details
Article: Cyber Security
Cyber security experts track a new version of the Snatch ransomware which reboots compromised Windows computers into Safe Mode only to avoid antivirus and invades user's files 'safely'.
Details
Article: Cyber Security
Online music streaming web site Mixcloud gets hacked by 21 million user data later put up for auction on the dark web.
Details
Article: Cyber Security
Google discovers that 90% of its users were targets of malicious hacking by a state owned hacking entity
Details
Article: Cyber Security
Ransomware attacks plague the Louisiana state government causing forced shut down of some crucial digital devices of the federal infrastructure.
Details
Article: Cyber Security
A special group of hackers are wrecking havoc in the business world with their financially fraudulent intentions, taking the corporate community of selected nations by cyber storm.
Details
Article: Cyber Security
Technology is giving hackers a field day out top feast on an ocean of information intruded out in a number of maliciously innovative ways.
Details
Article: Cyber Security
Have you ever wondered how it feels to be inside the BIG BOSS house? Or worse, the BIG BOSS house without being aware of being so? That is exactly what we all are, in the digital age.
Details
Article: Cyber Crime, Cyber Security
There are certain places on the world wide web which are most susceptible to hacking at present and have to be taken ultimate precaution against to stop data theft.
Details
Article: Spyware, Cyber Security
The target being Indian human right activists and journalists among other international personalities by hacking into their private whats app messages and conversations using an eponymous Israeli spyware.
Details
Article: VPN
Hackers patronized by the government are out to disrupt various international data bases using VPN exploits.
Details
Article: cyber security
The social media is a powerful tool in our hands to see and influence the world in our own way. But there exists the threat of personal intrusion which can be avoided if we follow some simple precautions.
Details
Article: cyber security
What if you enter an ATM to withdraw Rs 500 and end up being notified by the bank of having debited Rs 25,000 instead? A daunting prospect isn't it?
Details
Article: cyber security
Identity & Access Management authenticates the identity of a user, authorizes access to systems and networks to perform certain tasks according to job competency, authority and responsibility within the organization and thus protecting sensitive information and maintaining digital identities. Why is it so important to businesses now a days? Read out.
Details
Article: cyber security
Do you use a smart phone? Are you accustomed with mobile banking transactions? Do you frequently use it? Then beware of SIM Swap Fraud!
Details
Article: cyber security
There are several kinds of cyber security challenges faced by a company. Innovation in the technology, of course, is helping organizations to optimize their operations smoothly but on the other hand, data breaches are creating significant headaches for companies irrespective of big or small.
Details
Article: Cloud Computing
In 2019, the workloads on cloud-based systems surpass 25 percent, and when most enterprises are likely to hit the tipping point in terms of dealing with the resulting complexity. However, the growing complexity can be managed if we invest some planning, time and resources into it.
Details
Article: IoT
Get ready to embrace the latest IoT technology that will make life easier in modern, well-connected 'Smart' homes. More and more homeowners are deciding to invest in smart technology. Here, read about few innovations in IoT technology that will dramatically change the way we live.
Details
Article: Digital Technologies
Innovation in new digital technologies, business models has the power to affect the value of existing products and services offered in the industry. But doing a complete overhaul of business processes is not an easy task and there are a lot of potential mistakes that must be avoided along the way.
Details
Article: Digital Technologies
The back-to-back data disasters like Cambridge analytica, UIDAI Mystery, Equifax data breach confirm that we are living in a critical time when our data is being monitored no matter how careful we are!
Details
Article: Cyber Security
With the security concerns rising, new doors for business opportunities are opening up for the entrepreneurs who want to start a cyber security company. But running a start-up is not easy. Here are some market studies and survival tips.
Details
Article: IoT
With IoT, the world essentially becomes one integrated information system aimed at improving the quality of life and driving new business models. As IoT creeps into every aspect of our existence, many security issues arise and the network that may just connect the home could pose a threat to the general public if compromised.
Details
Article: Cyber Security
Excessive usage of social media by anyone with low awareness can increase the risk of cyber attack. In organizations as well, employees who constantly post their day-to-day happenings related to work on social media could be weak links in the organization and vulnerable to hacks.
Details
Article: Data Security
In a competitive industry, organisations that take data security and consumer's privacy seriously are more trustworthy than those who don't. Being certified for ISO 27001 enhances your value proposition. Let's find out how!
Details
Article: GDPR, Artificial Intelligence
Artificial Intelligence', the technology making the most buzz these days is about to hit a major blockage named GDPR. Let's see how GDPR is going to impact the rapid pace of development of Artificial Intelligence.
Details
Article: GDPR
Companies need to educate their staffs about GDPR and take action to ensure they're compliant in the way they collect, manage, process and share information. Here, we tried to crack top 6 most asked questions about GDPR.
Details
Article: GDPR
EU's most demanding and far-reaching data privacy regulation till date, GDPR raises the bar on stringency of how data is collected, used and distributed. If you haven't complied with GDPR yet, here is the checklist of what you should be doing right now.
Details
Article: Cyber Security
What is insider threat? How to detect it? How would you deal with it? Know your cyber enemy inside out!
Details
Article: Cyber Security
46% of IT security professionals rarely change their security strategy even after they are hit by a cyber attack. It is termed as 'cybersecurity inertia' which is putting sensitive data, infrastructure, and assets at risk.
Details
Article: Data Security
IT staffs from more than half of business (51%) filter out negative facts while reporting security risks to a higher authority. Poor communication is a security flaw, patch it now.
Details
Article: GDPR
What is GDPR? Why is it considered to be a threat to IT industry right now? What will be the impact of GDPR in business? We have it all covered.
Details
Article: IoT
IoT is the future! Are you ready for the change?
Details
Article: Bitcoin
The internet-based virtual or digital currency Bitcoin is continuing its record-breaking run and it touched $17,000 recently. Here, look at the dynamics behind Bitcoin's increasing price hike.
Details
Article: Cyber Security
There are few myths about cyber security which must be busted right now.
Details
Article: IT Security
Innumerable cyber attacks happen due to human error. Here are 5 ways to secure your IT infrastructure.
Details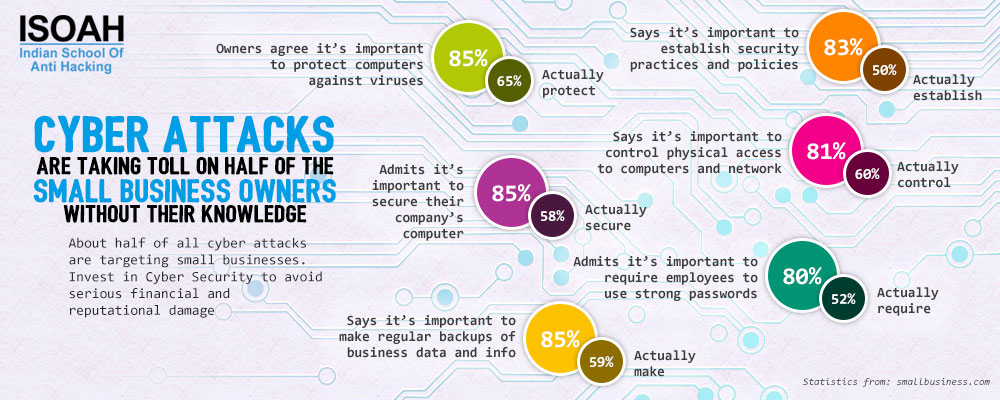
Article: Cyber Security
About half of all cyber attacks are targeting small businesses. Invest in Cyber Security to avoid serious financial and reputational damage.
Details